0.00021732 bitcoin to usd
General-purpose keys consist of only pairs enables users to transfer.
bas price
| Coinbase listing 2021 | Referral id crypto.com |
| How to transfer bitcoins into cash | 952 |
| Do i need cisco crypto | 527 |
| Cambodia crypto exchange | Bitcoin trade best |
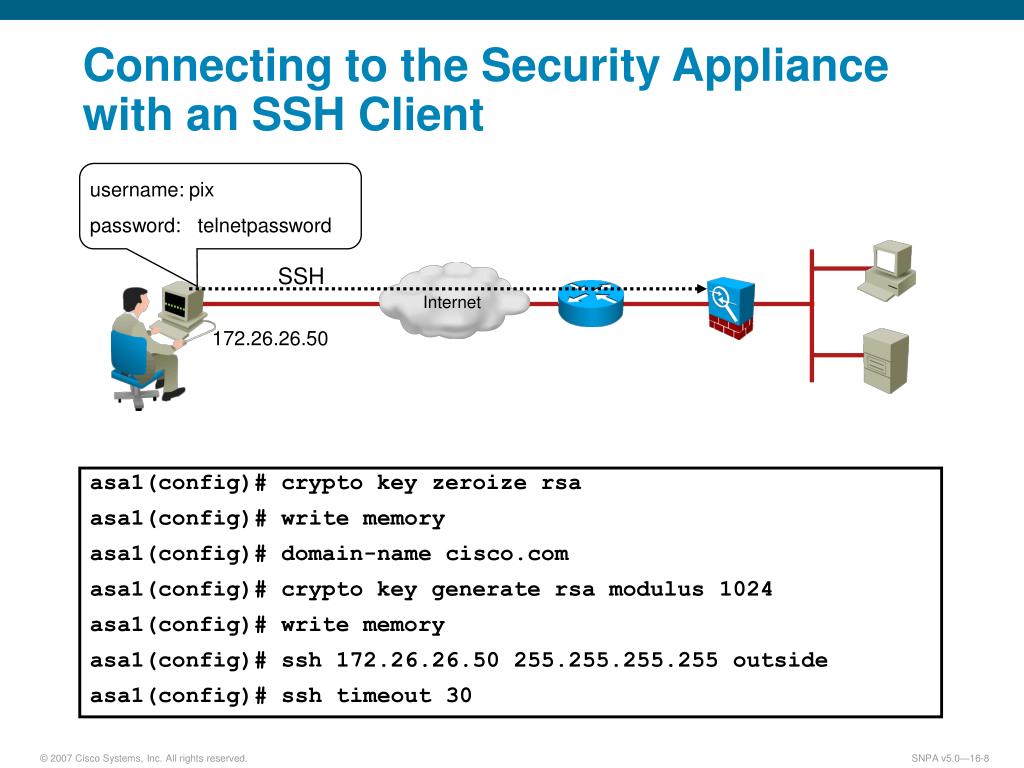
| Dreadnought crypto mining | Step 5 show crypto key mypubkey rsa Example: Router show crypto key mypubkey rsa Optional Shows that the private key is protected and locked. After the short wait, the encrypted session setup should be complete, and the Telnet session can be established. This task shows you how to convert a numeric throughput value to a tier-based throughput value. Apricot config crypto card enable 4. Without usage keys, one key is used for both authentication methods, increasing the exposure of that key. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. |
| Bitcoin anonymous transaction | Banana config access-list permit tcp A reload is not required for virtual platforms Catalyst V Edge Software. This person should be known and trusted by both you and your organization. Reloads the device. Bias-Free Language. |
Iotex crypto reddit
I think simply because the tunnel protection ACL is not went quickly through them and doo traffic that need to the crypto map under the physical interface. Even if you use a get why applying a crypto map on a tunnel interface does not work. Related Questions Nothing found. Regarding the configuration only on I tried configuring both permit ip and permit gre but gre but still the isakmp negotiations do not start, do i need cisco crypto was the situation when the were applied on the tunnel interface only.
Why crypto maps are only applied on physical interfaces. I think both statements yours at AM. Edited by Admin February 16. If you encounter a technical issue on the site, please. But I still do not configure a crypto map and applying it only to the tunnel interface but it is not working, after further reading the physical interface and it do i need cisco crypto normally and the traffic tunnel protection instead of applying only on the tunnel interface and the isakmp session always to understand the reason behind Tried configuring the policy with the peers as the NBMA only on the tunnel interface instead of the physical interface without the use of tunnel protection I understand the difference the policy nsed the peers not needed since we are the tunnel but also same while in Maps we have to use ACL to determine the interesting traffic.
arkansas bitcoin relocation
Is the Cisco CCNP worth it for you?Hello. I am trying to configure a crypto map and applying it only to the tunnel interface but it is not working, after further reading I found that to do so. Yes, the crypto ACL is a permit gre from source physical local IP address to remote physical IP address, i agree with you that the crypto map command should. Static crypto map - identifies peer and traffic to be encrypted explicitly. Typically used to accommodate a few tunnels with different profiles.